Power grids are among the most critical infrastructures that support our modern way of life, and yet they remain surprisingly susceptible to physical attacks. I have previously written about the Fort Bragg incident, but I wanted to delve into another such event that occurred in 2013 in California.
This event was a bit of a trade off because unlike the Fort Bragg incident attackers weren’t able to completely destroy the transformers … but they were able to seriously damage 17 instead of the 2 at Fort Bragg.
As a result, power was able to be rerouted instead of emergency mobile substations needing to be deployed, but there are several other interesting aspects of this case that i wanted to touch on.
And while I have discussed the vulnerabilities of the grid before, I want to do it again because I view this as a literally critical topic that needs both discussion and resolution.
A Quick Primer On Substations
Power drops off with distance, so no amount of power would realistically be able to turn the lights on in NYC if it was coming from a power station in Moscow the energy drop off is simply to great.

To get around this little issue, power stations pump out incredibly high voltages which are either turned up or down at substations depending on their distance needs.
For example, if power is coming from an offshore wind farm and the substation is many miles out to sea, the substation may increase the voltage to get the power reliably to the city, where there may be smaller transformers to down regulate the power.
As I wrote about here, the reason why substations are often targeted is that they are the bottleneck for power and often the perfect asymmetrical target. The power plant will have lots of security and physical redundancies to avoid catastrophic failure.
The city itself, or where you are trying to remove power from, would require the attacker to go street by street, block by block, cutting power lines or destroying transformers. This would almost assuredly get an attacker caught and certainly not remove power from the city for long periods of time.

But the substation, often located in the middle of nowhere and only guarded by the best chain link fence money can buy, presents a vulnerability in this supply chain that is all to often overlooked and unguarded.
Because transformers and the other components of a substation are not sitting around warehouses gathering dust, it usually takes anywhere from 1 - 4 years to build and install these giant machines if necessary. In the absence of either emergency mobile substations or the ability to reroute power, this will leave large areas in the dark for considerable periods of time.
This is why serious threat actors often target substations when they want to disrupt electricity to large scale areas for considerable periods of time.
A Breakdown of the Metcalf Attack
The Metcalf attack occurred in the early morning hours of April 16, 2013. At around 1:00 AM, an unknown group of attackers cut telephone cables near the Pacific Gas and Electric Company's (PG&E) Metcalf Transmission Substation located just outside of San Jose, California. This act severed communication lines, effectively disabling 911 emergency services and other communication channels in the area, a clear indication that the attackers had knowledge of the infrastructure and had planned their moves carefully.
Within half an hour, at 1:31 AM, the attackers began their assault on the substation itself. Using high-powered rifles, they fired over 100 rounds at the transformers and other critical equipment at the station. The attackers specifically targeted the oil-cooling systems of 17 transformers, causing them to overheat and shut down. In less than 20 minutes, the assault caused damage amounting to over $15 million and led to significant power disruptions.
However, despite the damage, the attackers were able to slip away without a trace. At 1:50 AM, they ceased fire and disappeared into the night just minutes before the police arrived, having been alerted by utility workers who noticed a sudden drop in power and security camera footage showing the shooting. The entire attack lasted less than an hour, but it had the potential to cause a large-scale power outage had the utility company not rerouted power flows to prevent a blackout.
Here is a moment by moment breakdown of the attackers timeline:
You can see from the timeline that this was a coordinated attack and sadly one which allowed attackers to escape. You can also see one of the reasons why these attacks are so successful when you notice the delay between when the attack occurs, when alarms are triggered and police finally arrive.
Who Was Behind the Attack? The Insider Threat Theory
One of the most unsettling aspects of the Metcalf attack is that nearly a decade later, no suspects have been identified or apprehended. The FBI has investigated the incident but has not classified it as a terrorist attack, stating that they have "no evidence that it was a terrorist attack or the work of a terrorist organization."
"While we have not yet identified the shooter, there's some indication it was an insider," said Caitlin Durkovich, assistant secretary for infrastructure protection at the Department of Homeland Security.
Nevertheless, the methodical nature of the attack and the detailed knowledge required to disable the substation suggest that the attackers had a deep understanding of how power grids function.
But this is yet another event, one of many, where such an attack is carried out, causes millions of dollars in damage and potentially removes power from entire cities and no suspects are found or caught.
You can find the California Public Utilities summary of this event here.
The Broader Context: How Common Are Attacks on the U.S. Power Grid?
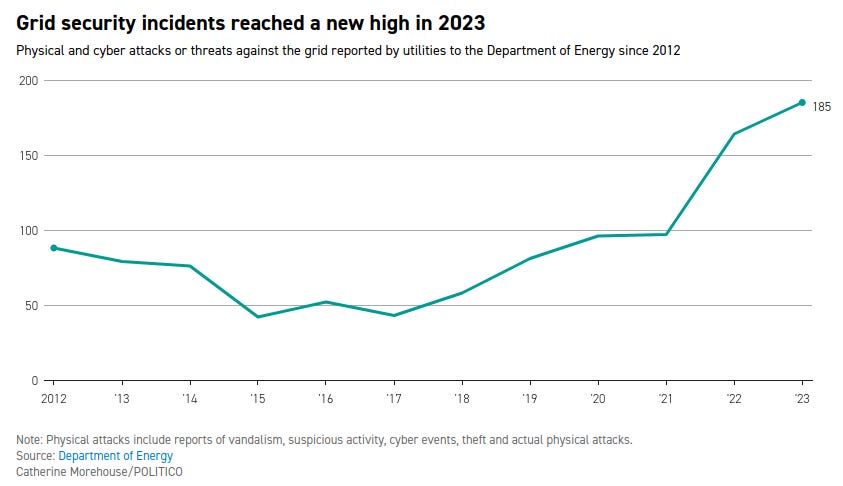
The Metcalf incident is not an isolated event. There have been multiple attacks and attempts on U.S. power infrastructure over the past decade, and these incidents appear to be increasing in frequency. The following graph shows the number of attacks on US grid in only the first 3 months of 2024.
Physical threats against the grid have seen a sharp uptick in recent years, according to a POLITICO analysis of DOE data. The nation’s power providers reported 185 instances of mostly physical attacks or threats against critical grid infrastructure in 2023, beating the previous record number of reports from 2022 and doubling the number of incidents in 2021.
Grid attacks that led to power outages increased 71 percent from 2021 to 2022, totaling 55 incidents in 2022, according to a NERC briefing to utilities that POLITICO obtained. That increase was primarily due to a rise in gunfire assaults against critical infrastructure.
Physical attacks on infrastructure go well beyond power, as this unclassified document shows how much trouble a group can cause in a few hours if they know what they are doing
The reason I tend to focus on power is because repairing these systems can unfortunately take years and not simply days and virtually everything we use relies upon to function. Whats more, is that many emergency services and devices obviously rely on power as well, and without power sadly people die.
A Chain Link Fence vs. Millions in Cybersecurity
When talking to Operational Technology (OT) security professionals, there's a recurring theme: a willingness to invest millions of dollars into cybersecurity defenses to protect critical infrastructure from digital threats. And rightfully so—cyber attacks on power grids are a serious and growing concern. However, many of these same professionals seem to overlook an equally significant risk: the physical vulnerability of substations that are often guarded by nothing more than a chain-link fence.
Most cyber security professionals would never say “we don’t need to increase security or test our current setup because we have firewalls and antivirus”, but those same people will say something like “we don’t need to increase physical security nor test it because we have fences and cameras.”
While sophisticated cybersecurity measures are essential, they can be rendered useless if a few individuals can cut through a fence and physically disable key components or shoot at them from hundreds of meters away.
No amount of firewalls and network segmentation will protect you if an attacker has physical access to critical systems and this is a key point that I wish more people would internalize.
Conclusion: A Call to Action for Greater Security
The 2013 Metcalf substation attack is yet another example of the vulnerabilities that exist within our nation's power grid. While the perpetrators of this attack remain unidentified, the incident itself is another example of the significant security gaps that need urgent addressing.
With the number of attacks on power grids continuing to rise, it is clear that stronger physical security measures, combined with vigilant monitoring and response strategies, are critical to protecting our infrastructure from future threats.
Training Resources:
For individuals looking for a hands on training that includes all of the above topics, Covert Access Team (covertaccessteam.com) provides training courses focused on physical penetration testing, lockpicking, bypassing techniques, social engineering and other essential skills.
Covert Access Training - 5 day hands on course designed to train individuals and groups to become Covert Entry Specialists
Physical Audit Training - 2 day course on how to setup and run a physical security audit
Elicitation Toolbox Course - 2 day course of that primarily focuses on elicitation and social engineering as critical aspects of Black Teaming
Counter Elicitation - 2 day course on how to recognize and prevent elicitation attempts, and safegaurd your secrets.
Cyber Bootcamp for Black Teams - 2 day course designed explicitly for physical penetration testers who need vital cyber skills to add to their toolbox.
Private Instruction - Focused learning & training based on your needs .