While this blog focuses primarily on Covert entry and penetration testing, I find myself more often dealing with clients who have been the victims of very Overt crime. So today this blog post will focus on a particular type of such crime, the theft of industrial equipment for use in other, usually larger crime.
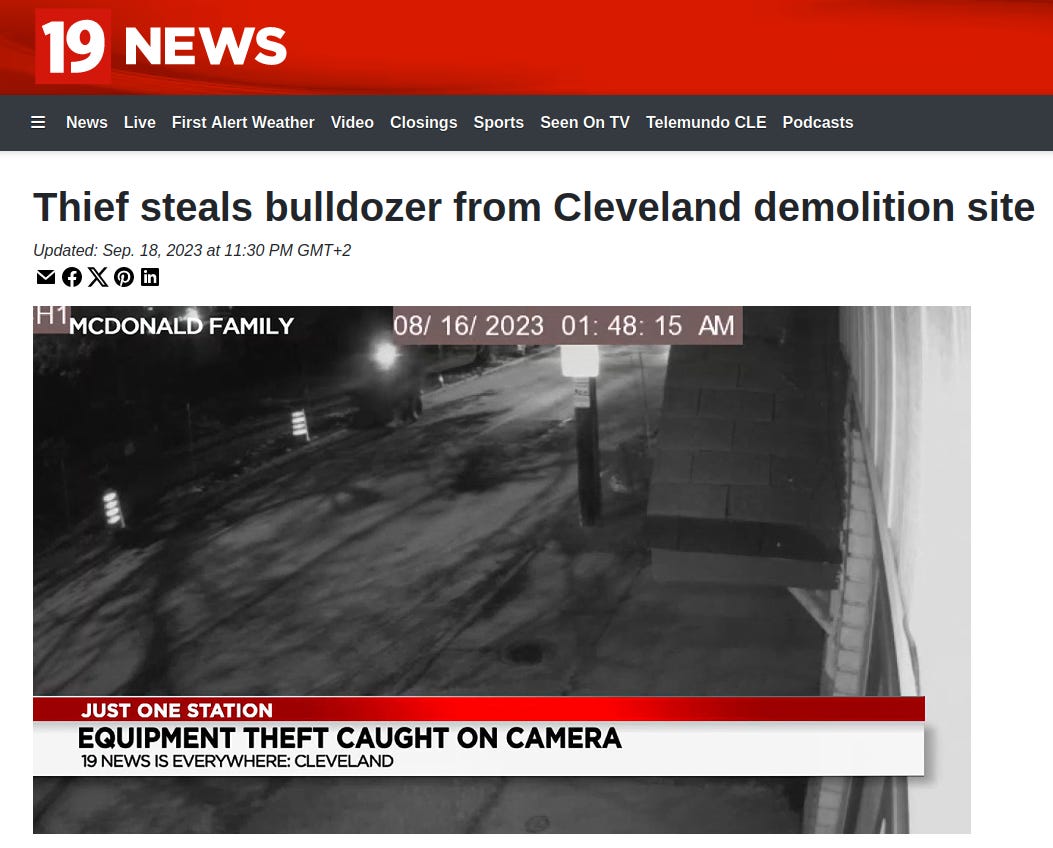
Imagine a bulldozer, usually a symbol of construction and development, being repurposed as a tool for crime—such as tearing a safe from the wall of a bank. This disturbing transformation of heavy machinery from a force for good to an instrument of theft highlights a broader issue in the realm of crime: the innovative ways in which criminals exploit seemingly benign tools for nefarious purposes. But how do these industrial giants, designed for constructive work, fall into the wrong hands so frequently? A significant part of the problem lies in their surprisingly vulnerable security measures.
The video below shows a gang who have stolen a self moving crane in order to breach and steal an ATM.
The Surprising Vulnerability of Industrial Equipment
A startling fact not widely known outside of the construction and manufacturing, police and insurance sectors is that many pieces of industrial equipment, such as dozers and excavators, are either keyed alike or use universal keys that can operate multiple machines. This means that one key can start a variety of machines across different sites and even different brands. These master keys are not only simple in design but are also readily available for purchase online, often without stringent checks on the buyer’s intent.
The intention behind such universal keying is to streamline operations on job sites, reducing the burden of carrying a large set of keys. However, this convenience also presents a significant security risk. It has been reported that these universal or master keys are easily accessible, making it trivial for thieves to operate these machines without authorization (National Equipment Register, Construction Equipment Theft Recovery Report).
Its not just industrial equipment that are keyed like or use master keys, the list of such things include:
Cabinets
Fleet cars such as old police crown vics
Elevators
Alarm systems
Telephony systems
Industrial equipment
Interchangeable construction site locks
and more
The Exploitation of Weak Security
The simplicity of the keys for these machines adds another layer of risk. Unlike modern car keys, which include features like programmable chips and magnetic coding, keys for heavy machinery are rudimentary and easy to duplicate (usually). This lack of sophisticated security features means that not only can legitimate users easily replace lost keys, but criminals can also effortlessly gain access to the machines.
The consequences of this security flaw are not limited to the theft of the machinery itself. Once obtained, these machines can be used in crimes ranging from ATM smash-and-grabs to breaking through the walls of businesses or even as battering rams in more complex criminal operations. The power and size of these machines make them ideal for executing large-scale crimes efficiently.
A Look at the Statistics
The statistics surrounding industrial equipment theft and its use in crimes paint a grim picture. According to the National Equipment Register (NER), equipment theft is a billion-dollar industry with shockingly low recovery rates. Only about 20% to 25% of stolen construction equipment is recovered annually, which is much lower than recovery rates for stolen cars (National Insurance Crime Bureau).
The National Crime Information Center (NCIC) further reports an increase in the use of heavy machinery in criminal activities, highlighting a 10% rise over the past five years (FBI-NCIC Database). These statistics underscore the growing trend among criminals to leverage these powerful tools for committing significant and audacious thefts.
Increasing Incidents in London
In London, the rise in the theft of and the criminal use of industrial equipment has become a notable concern for law enforcement and construction companies alike. Reports from the Metropolitan Police and local news sources indicate that the incidence of these crimes has seen a significant uptick over the last few years. A 2021 report highlighted a 15% increase in the theft of heavy machinery within the Greater London area compared to previous years (London Police Department Annual Report).
For instance, a notable case reported by the BBC involved the use of a stolen excavator to remove an entire ATM from a shopping centre wall in East London (BBC News). This incident is just one example of how such equipment, intended for constructive use, is being repurposed for large-scale thefts.
The MET police include a website for both preventing and mitigating such crime which you can read here.
Smaller Tool Theft
Image from hertstools.co.uk
Its not just large industrial equipment that is being stolen and used for crime, but smaller tools and building material have also seen a sharp rise over the last few years.
According to Hertstools “In London alone, 34,712 tools were stolen from January 2021 to October 2021.” which is a 150% rise from only 2 years ago, which was already at a very high level.
What is more discouraging though would be that
“In over 86% of cases, the suspect is never identified.”
Keep in mind that while these smaller tool thefts are usually immediately sold off at illegal markets, they can and are also used for other larger crimes.
The video below shows an illegal market of stolen construction equipment that likely constitutes hundreds of thousands of dollars of stolen property and is sadly a common occurrence
Conclusion
The escalating trend of industrial equipment and tool theft presents a significant challenge, not just to the construction and manufacturing industries but to the broader community as well. The ease of accessing universal keys and the simplicity of machinery operation has emboldened criminals, turning tools and heavy machinery into instruments of large-scale theft and vandalism. Addressing this issue requires a concerted effort involving improved security measures, legislative action, and increased awareness among equipment owners.
Training Resources:
For individuals looking for a hands on training that includes all of the above topics, Covert Access Team (covertaccessteam.com) provides training courses focused on physical penetration testing, lockpicking, bypassing techniques, social engineering and other essential skills.
Covert Access Training - 5 day hands on course designed to train individuals and groups to become Covert Entry Specialists
Physical Audit Training - 2 day course on how to setup and run a physical security audit
Elicitation Toolbox Course - 2 day course of that primarily focuses on elicitation and social engineering as critical aspects of Black Teaming
Counter Elicitation - 2 day course on how to recognize and prevent elicitation attempts, and safegaurd your secrets.
Cyber Bootcamp for Black Teams - 2 day course designed explicitly for physical penetration testers who need vital cyber skills to add to their toolbox.
Private Instruction - Focused learning & training based on your needs .





Great post, Brian! Installing remote gateways, embedded processors, GPS tracking, motion sensors, cameras, and/or Electronic key fob security technology on industrial heavy equipment is a cost-effective investment. These additions can be seamlessly integrated into the manufacturer's overhead or offered as an optional security package for clients. The onboard remote monitoring equipment educates customers on configuring Networking, Security, and Tracking features upon purchase.
The same concept that has been added to passenger vehicles should be implemented, treating machinery like an IP-based endpoint. Construction managers gain control over operations, setting schedules, geofencing, and user access via account/fob permissions. Instant notifications via a mobile app allow quick response to unauthorized use. Managers can identify the machine's location, user, and disable it remotely if needed.
Ensuring the security of onboard hardware is paramount to prevent easy tampering. The growing demand for skilled engineers and technicians in OT Security highlights the importance of applying robust security measures to construction machinery and beyond.
This approach underscores the significance of security convergence, —bridging physical, cyber, OT, and IT realms, as you well know. Organizations benefit from a holistic perspective, moving away from traditional siloed approaches.