From Communication to Compromise
Analyzing Weaknesses in RFID Access Control Systems
In the realm of physical penetration testing, RFID (Radio Frequency Identification) access control systems are very common, and also very misunderstood.
The general thinking seems to be that an Access Control System functions with only one “language” and one frequency, in reality both of these are wrong, and for the purposes of Black Teaming, understanding this error is a vital tool.
The most common attacks on RFID access control systems are:
Cloning the ID card
Spoofing the ID card
Attacking the card reader (often replay attacks)
The misunderstanding on how Access Control Systems work is what allows Black Teams and attckers to abuse various vulnerabilities to perform the types of attacks I listed above. Lets explore some of the vulnerabilities and how these systems work.
High Level - Duel Languages
Their are two communications “languages” or protocols used when discussing most Access Control Systems, the one between the card and reader (in blue) and the one between the card reader and controller (in green).
Lets Start with the Card & Card Reader
Before we talk about the protocols / language used between devices, lets understnd the frequency those languages will be transmitted on. 99% of the time, there are two frequences used, High and Low.
High and Low-Frequency Cards and Readers:
Low-Frequency (LF) Cards and Readers: Low-frequency cards (125 kHz) are known for their inherent insecurity. Presently most are completely cryptographically broken and the cards easily clonable
High-Frequency (HF) Cards and Readers: High-frequency cards (13.56 MHz) offer a more secure option compared to low-frequency cards. While there are more security in High Frequency cards, there are many popularly used card types that are easily clonable.
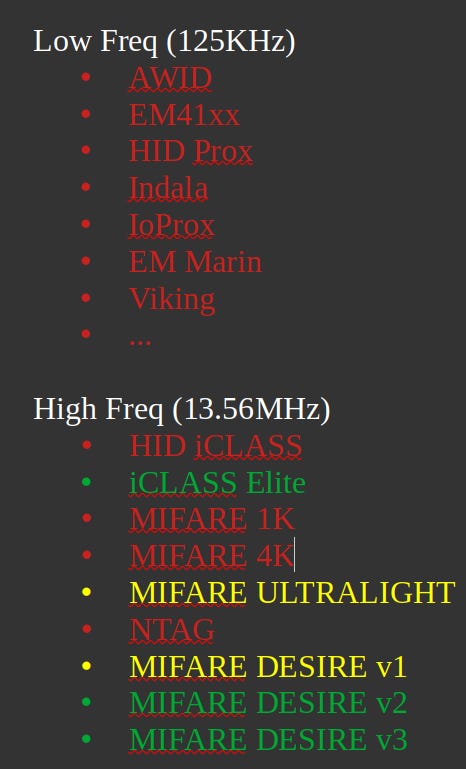
To quickly understanding the difference in security offered between Low and High frequency cards, look at this chart
Red = broken or no security (CLONABLE CARDS)
Yellow = somewhat safe, (CLONABLE CARDS BUT TRICKY)
Green = safe), (UNCLONABLE CARDS)
Black Team members can use tools such as an RF field detector to quickly discover what frequency the reader is using, and if the building is using Low Freq, its almost a guaranteed win.
The Reader to the Controller
The communication between card readers and controllers in RFID systems often relies on the outdated Wiegand protocol, which was developed in the 1970s. This protocol is known for its inherent insecurity, creating opportunities for exploitation.
Intercepting and Replay Attacks: Attackers can intercept and replay communication between card readers and controllers using devices like ESP keys. This interception and replay capability bypasses the access control system, granting unauthorized access to secured areas.
Inadequate Encryption and Authentication: The Wiegand protocol lacks robust encryption and authentication mechanisms, making it susceptible to eavesdropping and unauthorized data manipulation. Attackers can exploit these weaknesses to gain unauthorized access or tamper with the system.
Wiegand is the most common protocol / language used today between the card reader and controller.
This diagram shows the security levels of backend languages
Red = Broken (REPLAY ATTACKS POSSIBLE)
Green = Safe (REPLAY ATTACKS NOT POSSIBLE)
This means that even if you are using an unclonable Mifare Desfire v2 but the backend language is Wiegand (the most commonly used backend language), you still are vulnerable to attacks.
This can be attacked with tools such as the ESP key, which sits between the card reader and controller to intercept and replay the insecure Wiegand data.
Exploiting Tamper Detection Switches
Tamper switchs are built in mechanisms inside the card reader to alert security if the card reader is opened or tampered with. However, these switches are often improperly installed or entirely absent, creating a significant vulnerability.
Physical Attacks and Unauthorized Access: Neglected or absent tamper detection switches allow attackers to tamper with the card readers without detection. Physical attacks, such as bypassing the card reader or accessing internal components, become significantly easier, leading to unauthorized access.
Compromised System Integrity: Tampering with card readers compromises the integrity of the access control system. Attackers can manipulate or disable the readers, rendering the entire system ineffective and exposing it to further exploitation.
If you want to take a card reader apart, most of the more comon brands will be removed via a screw on the bottom of the reader.
Conclusion
RFID access control systems, while widely adopted, pose inherent vulnerabilities that can be exploited by attackers. Understanding the dual communication methods, the security implications of high and low-frequency cards and readers, the weaknesses in the card reader-to-controller communication, and the importance of tamper detection switches is crucial for black team and physical penetration testers.
Identifying and addressing these vulnerabilities helps enhance the overall security posture of RFID access control systems, ensuring they provide robust protection against unauthorized access and exploitation.
Training Resources:
For individuals looking for a hands on training that includes all of the above topics, Covert Access Team (covertaccessteam.com) provides training courses focused on physical penetration testing, lockpicking, bypassing techniques, social engineering and other essential skills.
Covert Access Training - 5 day hands on course designed to train individuals and groups to become Covert Entry Specialists
Elicitation Toolbox Course - 2 day course of that primarily focuses on elicitation and social engineering as critical aspects of Black Teaming
Cyber Bootcamp for Black Teams - 2 day course designed explicitly for physical penetration testers who need vital cyber skills to add to their toolbox.