The vulnerabilities within Europe’s power grid have presented a tantalizing opportunity for would-be attackers, particularly those with the sophistication and resources to execute a large-scale disruption. By leveraging weaknesses in outdated systems such as Radio Ripple Control, malicious actors have the potential to gain unauthorized control over up to 60 gigawatts (GW) of electricity—enough to cripple a continent. This exploration outlines how such a breach could be orchestrated, detailing technical entry points, potential impact, and the tools required to exploit the system.
All of this came from a recent research presentation from Germany, the full hour long presentation of this research can be watched here, which i encourage everyone to go and watch. The images used in this post are all from the presentation.
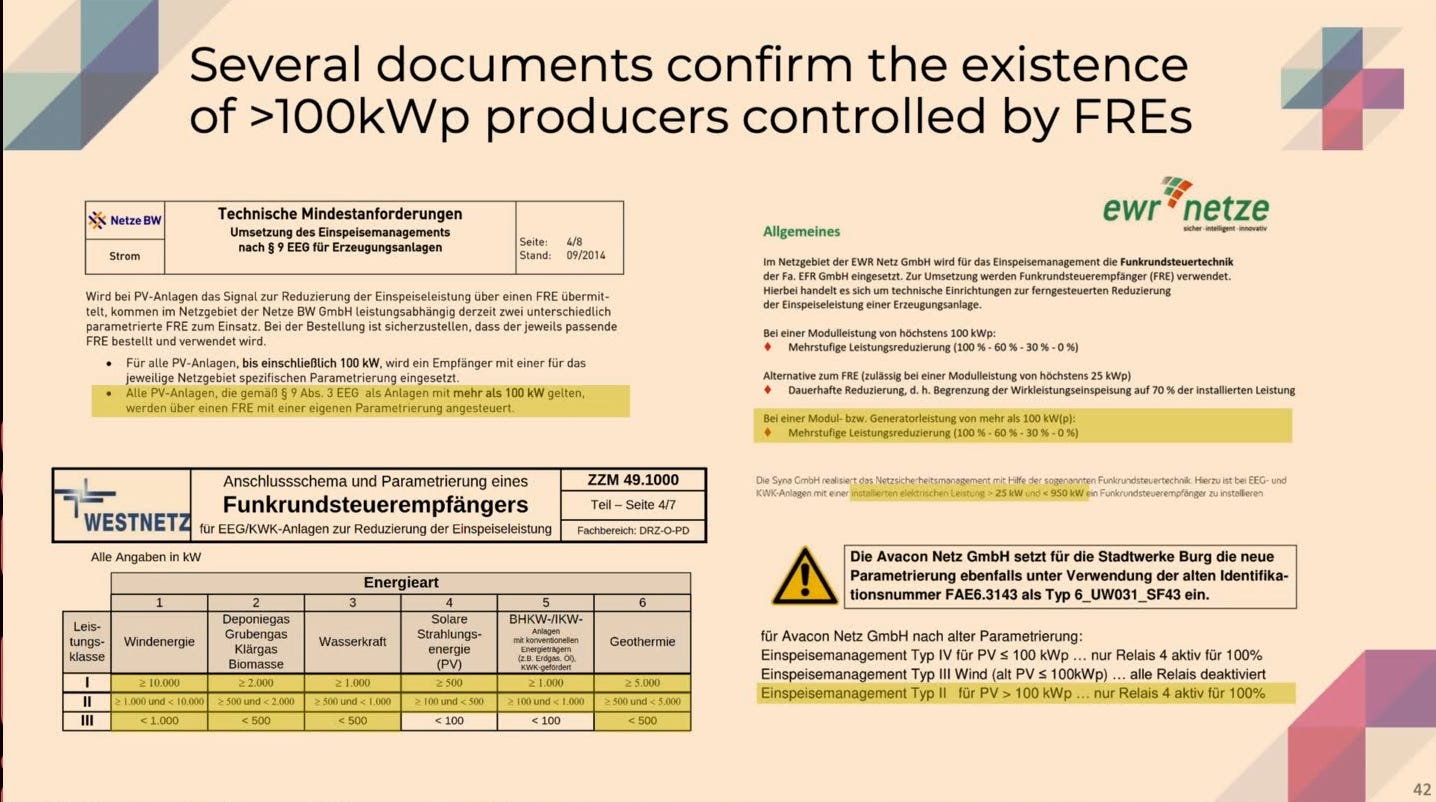
Around 300 companies in Germany have access to send commands directly to broadcasting towers, which will then utilize something called radio ripple control receivers, which would then either connect or disconnect a supply to the grid.
According to the researchers, the kinds of things that this process controls are … well a lot of things.
Lets start from the beginning and get into more details.
Turning a Curiosity into an Exploit
As demonstrated by researchers Fabian Bräunlein and Philipp Melette, exploiting weaknesses begins with understanding the system. Initially curious about controlling Berlin’s streetlights, the pair soon uncovered that these same systems managed far more critical infrastructure across Central Europe. Streetlights were merely the tip of the iceberg; the protocol they targeted also controlled regional power grids, renewable energy facilities, and load-balancing systems.
By capturing and analyzing legitimate radio signals, attackers could effectively replay or manipulate commands to take over connected systems. In Germany alone, these systems control 40 GW of renewable energy input and 20 GW of load management (e.g., heat pumps, EV chargers). With 60 GW under control, attackers could manipulate power generation and consumption on an unprecedented scale.
Understanding Radio Ripple Control
The outdated Radio Ripple Control protocol, still widely used across Europe, operates on unencrypted, frequency-modulated radio signals to send commands to power grid components. This system dates back to the early 1900s and relies on frequency-shift keying (FSK) to encode instructions. However, the lack of encryption or authentication means that anyone with the right equipment could intercept, analyze, and inject rogue commands into the grid.
For an attacker, gaining control begins with purchasing the necessary equipment. Bräunlein and Melette demonstrated that a basic software-defined radio (SDR) and an ESP32 microcontroller with a waveform generator are sufficient to emulate commands. By decoding the protocol’s languages, Versacom and Semagyr, attackers can craft their own malicious messages. This reverse engineering can be completed with publicly available documentation and reverse-engineering hardware.
In this case, the researchers were able to disable power going into the grid with nothing more than a flipper and some custom code
Maximum Disruption: Strategic Attack Points
Apparently, there is more than 60 gigawatts that are currently in control by the radio ripple protocol (which would all be effectively vulnerable to this attack vector. Keep in mind that this is only looking at Germany but likely applies to many other countries.
From the perspective of a determined attacker, the potential for damage hinges on exploiting three critical factors:
Unencrypted Signals: Radio commands used by energy providers are sent without any confidentiality or authentication. This makes them easy to intercept and replay, enabling unauthorized control.
Control Points Across the Grid: Attackers could target systems that manage load distribution and renewable energy input, creating severe imbalances in supply and demand.
Systemic Weakness: By timing attacks strategically—for example, during high-demand periods—attackers could amplify the impact of their actions.
According to the researchers, it will take MUCH LESS than 60GW in order to cause a serious grid based problem. The grid frequency is incredibly important, and it must stay, at least in Germany at 50 hertz, even slight variation, means any of the following issues will occur.
50.2 Hz or higher: Supply reduction triggered (e.g., turning off solar parks).
Below 49.8 Hz: Reserves activated; industries disconnected; hardware failures start
49 Hz or lower: Automated load shedding begins; 50% shed at 48.5 Hz, leaving 200+ million people without power.
47.5 Hz: Power plants disconnect to avoid damage; grid requires a full rebuild.
An optimally crafted series of commands could destabilize the European grid. For example, overloading lines in one region could lead to cascading failures, similar to the 2006 blackout caused by a single line being taken offline during a cruise ship transport. The researchers estimate that manipulating 60 GW could drop the grid frequency enough to trigger widespread automated shutdowns, cutting power to over 200 million people.
Tools and Techniques: What an Attacker Needs
Intercepting Radio Signals: An attacker would first tune into the frequencies used by transmitters, such as those managed by EFR, which oversees critical power communication in Germany and Hungary. By using a software-defined radio to listen to signals, attackers can identify command patterns.
Building Rogue Transmitters: To override legitimate signals, an attacker could construct high-powered rogue transmitters using antennas suspended by kites or weather balloons. This technique has been used by radio enthusiasts for decades and could enable attackers to broadcast commands over large distances.
Hacking Transmitters: Alternatively, attackers could directly compromise EFR’s systems by exploiting vulnerabilities in the desktop apps used by energy providers. Physical breaches of transmitter facilities are also possible, as security measures are reportedly minimal.
Flippers: you always need your trusty flipper
In the following video you can see the researchers using a kite tethered with copper cable to simulate their attack vector (though they did try a drone at first which failed).
Obviously this attack vector wouldn’t really work, as the attackers would quickly be caught … though if it were a real attack the damage would already have been done, and it is unlikely that police would immediately know that a few guys flying a kite are the cause of the entire city going dark in real time.
Towards the end of the presentation, the researchers mentioned THE MOST LIKELY ATTACK VECTOR to succeed and I couldn’t help but get a little smile across my face.
Sadly the some of the best times to trigger this type of attack, when it comes to attacking solar and wind, is to wait for a really sunny or windy day. And attackers could use tools in Germany that are open to everyone which shows how many such systems are currently offline in order to keep the grid from overloading
Having the ability to switch such systems on or off at will, gives attackers a lot of options when it comes to how to go about executing this attack.
According to the researchers the amount of power they may actually have access to is the largest unknown, as they are relying on open source data which may not be 100% accurate. However, in my opinion, it doesn’t really matter since they will certainly have more than enough power to cause city wide, or even country wide outages or disruptions.
Conclusion: A Fragile Target
Europe’s power grid, while robust in some respects, is dangerously exposed due to outdated technology and inadequate security measures. While the researchers stressed that these attack vectors are most likely to be exploited by state actors and not your typical script kiddie, it doesn’t change the fact that there are state actors who are likely aware of these attacks and would certainly have the means to exploit them.
I highly encourage everyone who reads this blog to go and watch the full presentation of the original research here. While I usually try to add some ideas for how to resolve these types of issues that I present, I honestly have no idea how this could be quickly fixed. Anything at this scale, and involving government involvement, will inherently be slow on the scale of years to decades, which leaves Europe rather exposed on this one.