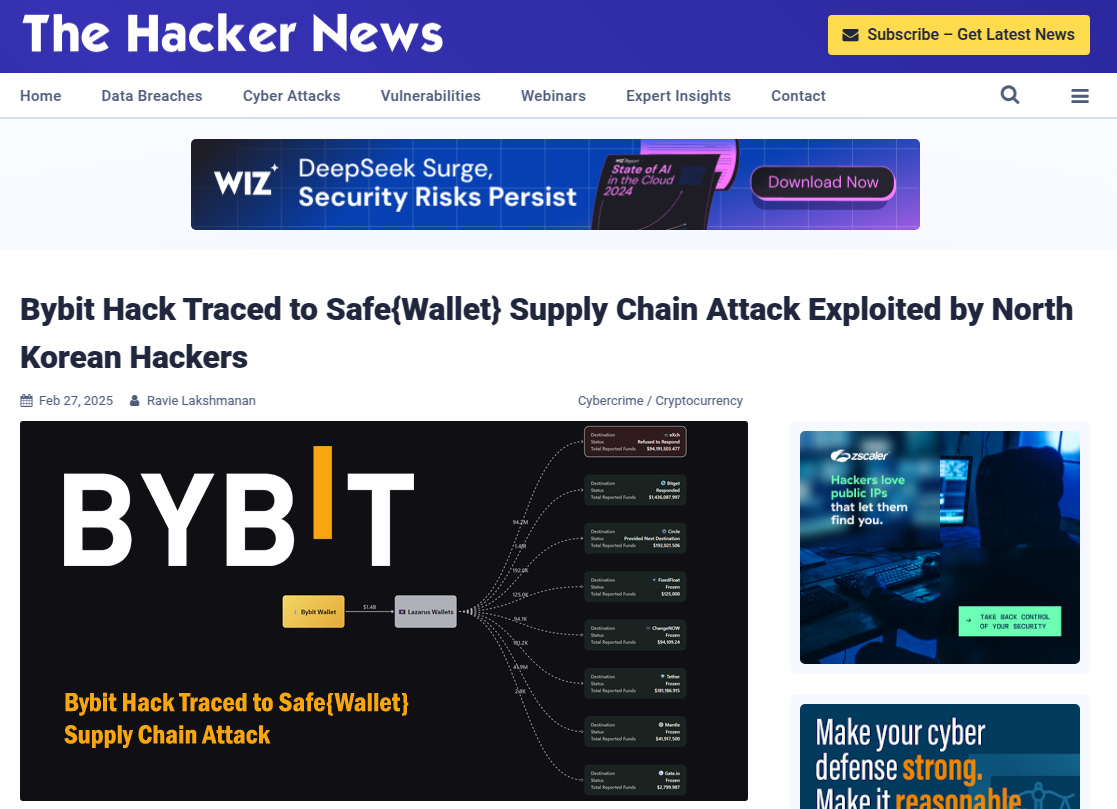
The recent revelation by the FBI that North Korean state-sponsored hackers were behind a $1.5 billion breach of cryptocurrency exchange Bybit has sent shockwaves through the cybersecurity community and financial sectors alike.
The Incident at a Glance
On February 26, Reuters reported that the FBI has attributed the massive hack to North Korea, with evidence pointing directly to the notorious Lazarus Group—a threat actor infamous for its high-profile cyber operations.
According to the report, “The FBI said North Korea was responsible for a $1.5 billion hack on Bybit, part of an ongoing pattern of state-sponsored cybercrime.” This bold assertion not only underscores the audacity of the hackers but also places the breach in a broader geopolitical context, where cyberwarfare increasingly blurs the lines between criminality and state-sanctioned aggression.
The incident was accomplished in a single heist in a matter of minutes last Friday and over the weekend, security groups were able to track money laundering in real time through various accounts associated with NK agencies.
It should be noted that this heist has yet to be investigated or confirmed by the FBI
Bybit’s CEO Ben Zhou has said that the company is still solvent and this event will not hinder trading by the companies 40 million users. It should be noted that Zhou actually put out a bounty on the group believed to be responsible for the heist
Inside the Cyberattack
As detailed by The Hacker News, investigators traced the hack to a supply chain vulnerability linked to SafeWallet, a trusted partner integral to Bybit's operations. This vulnerability served as the gateway for the attackers, allowing them to infiltrate the system without immediate detection. The article noted, “The Bybit hack was traced to a SafeWallet supply chain flaw, underscoring the need for rigorous third-party risk management in the crypto ecosystem.”
Further insights from CSO Online highlight that the Lazarus Group, known for its sophisticated techniques, may have exploited this vulnerability to access confidential data and siphon off billions in digital assets. The CSO analysis emphasizes that such attacks are not merely opportunistic but are part of a larger, strategic campaign orchestrated by state actors to undermine financial stability and gain economic leverage.
Who is the Lazarus Group?
The Lazarus Group is a notorious state-sponsored hacking organization linked to North Korea and has been active for over a decade. The group is believed to be an arm of Bureau 121, the cyber warfare division of North Korea’s Reconnaissance General Bureau (RGB). It has been implicated in some of the world’s most high-profile cyberattacks, ranging from financial heists to disruptive cyber warfare campaigns.
According to Fox-IT, a cybersecurity firm that has closely tracked the group’s operations, the Lazarus Group is responsible for cyber espionage, financial theft, and destructive attacks, all serving North Korea’s strategic and economic goals. Their activities have evolved significantly, from targeting South Korean entities in the early 2010s to executing global-scale financial crimes in recent years.
Notable Cyber Attacks by Lazarus Group
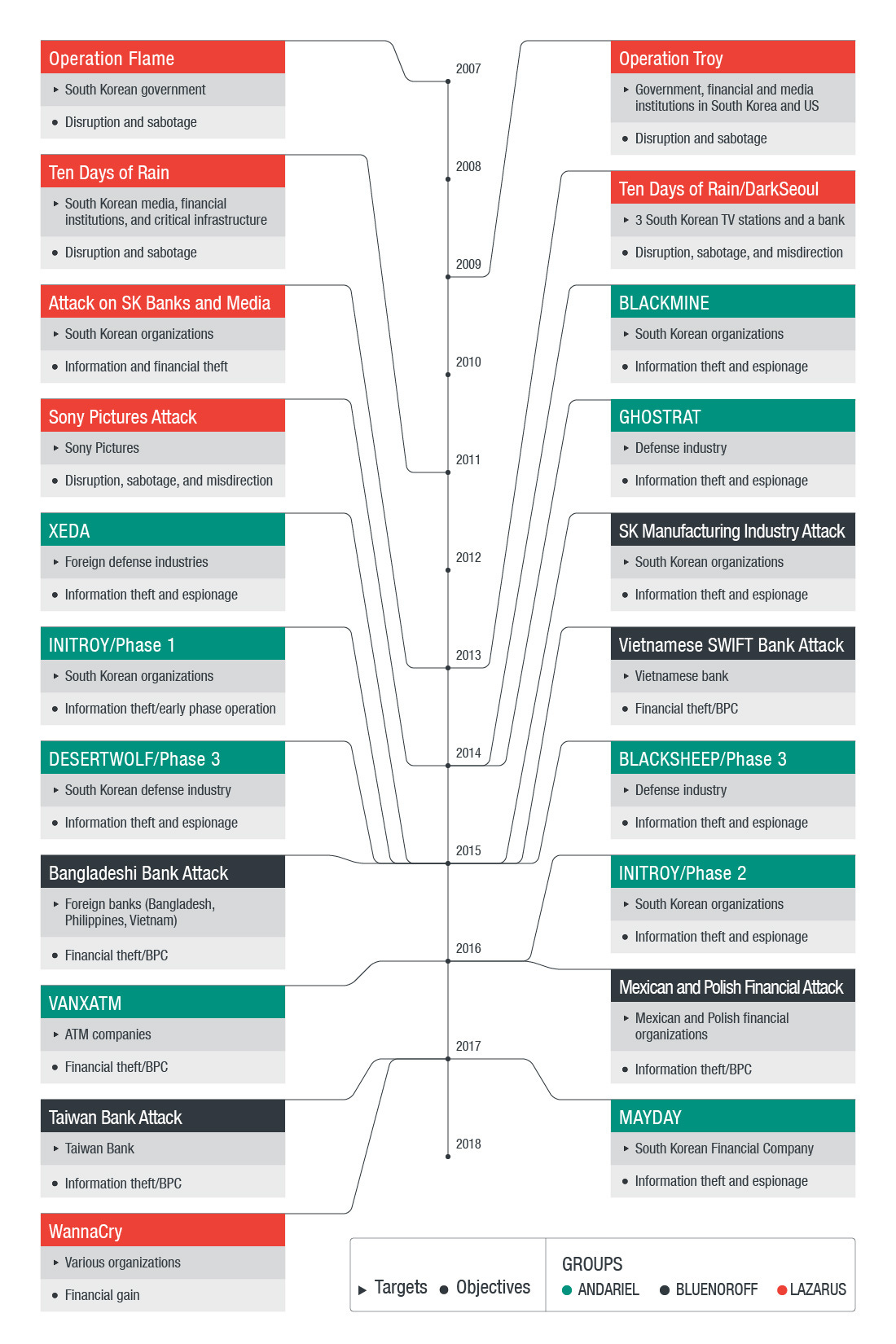
The Sony Pictures Hack (2014): One of their earliest known attacks, the Lazarus Group launched a massive cyber assault on Sony Pictures in retaliation for the release of The Interview, a comedy film satirizing North Korean leader Kim Jong-un. The attack resulted in leaked confidential data, emails, and the destruction of company servers.
The Bangladesh Bank Heist (2016): The group attempted to steal nearly $1 billion from the Bangladesh central bank through fraudulent SWIFT transactions, successfully siphoning $81 million before the breach was detected. This marked their shift towards large-scale financial cybercrime.
WannaCry Ransomware (2017): A global ransomware attack that infected hundreds of thousands of computers in over 150 countries, encrypting files and demanding ransom payments in Bitcoin. The U.S., U.K., and other governments attributed the attack to the Lazarus Group.
Cryptocurrency Heists (2020–Present): Lazarus has increasingly focused on crypto exchanges and DeFi platforms, exploiting weaknesses to fund North Korea’s weapons programs. Notably, in 2022, the group stole $620 million in Ethereum from Ronin Network, a blockchain associated with the game Axie Infinity.
the following chart of the group’s activities, between 2007 & 2018 comes from Trendmicro
Tactics and Techniques
The Lazarus Group employs a variety of sophisticated cyber techniques, including:
Phishing & Social Engineering: They often disguise themselves as recruiters or investors to infiltrate companies and install malware.
Supply Chain Attacks: As seen in the Bybit hack, Lazarus exploits third-party services to gain access to their targets.
Zero-Day Exploits: The group has leveraged previously unknown vulnerabilities in software to breach secure networks.
Money Laundering via Crypto Mixers: Lazarus uses Tornado Cash and other crypto-mixing services to obscure stolen funds before cashing out.
The Geopolitical Implications
This incident has far-reaching implications. North Korea’s involvement, as asserted by U.S. authorities, is a stark reminder of how nation-states are leveraging cyber capabilities as a tool of modern warfare. The Reuters piece also referenced an ominous moniker—“TraderTraitor”—hinting at the possible rebranding of cybercriminal personas to serve geopolitical narratives.
As explained in the Deccan Herald’s feature, “How North Korean Hackers Pulled Off the Biggest Heist in History,” the elaborate tactics employed by these hackers are a testament to a new era where traditional borders are irrelevant, and digital territories are the new battleground.
It is worth noting that according to TRM, in 2024 NK was able to pilfer around 800 million dollars, while this single heist doubled their entire annual theft from last year.
According to Fox-IT
“In December 2020, the U.S. Department of Justice filed charges against three North Korean hackers for stealing $1.3 billion in cryptocurrency, among other things. Whether it will ever come to arrests and trial, let alone deter Lazarus, is highly unlikely. Not much can be expected from politics either.”
Given that these criminals are operating under the direction of the NK government and even if they weren’t it would be very unlikely that NK would ever extradite anyone to the West, this group is very likely going to continue its activities for the foreseeable future.