A Return To Keyboxes
How often do we overlook the simple things? The mundane items that blend into the background yet hold the keys—literally and figuratively—to unlocking a breach?
We all know keyboxes from things like Air B&B or similar apartment sharing services and have come to expect seeing them. During an engagement, black teams will often take advantage of these boxes, because they are incredibly insecure and can be covertly breached within seconds.
Knowing this, why I am discussing keyboxes? Because there is a second type of keybox that people sometimes don’t consider when preparing for a breach, and that is the internal keybox, of the ones that are setup inside the building to act as a type of two factor authentication.
Once inside a target building, you may find that the client has done their due diligence to prevent anyone with access to the building or office from gaining access to the most sensitive areas or items.
Often these are things like: server or archive, classified or sensitive document lockers, or anything that the average employee shouldn’t have access to.
Here I will discuss what you might expect to find when encountering these boxes, and how you can abuse them to privilege escalate.
The Classic External Keybox: A Known Quantity
The most familiar keybox is the one mounted outside buildings, a hallmark of Airbnbs and commercial properties alike. These small, combination-secured boxes hold physical keys or fobs to grant easy access for authorized users. For black teams, breaching these devices is a straightforward task.
If you want an in depth step by step of how to go about it, you can find that here.
But in essence, decoding these boxes with any thin piece of metal is quick and requires little skill, just practice.
That said, there is one issue with these boxes that black teams need to be aware of and plan for, and that is which box is authorized.
For example, suppose you find yourself on an engagement, go to the target building during recon and find this … which box will you attack? Keep in mind that breaking into the wrong box is likely illegal.
Another thing to note with the image above is the variety of box types. None of the above are overtly challenging to breach, but they all require a different specific skill type and practice.
I highly encourage all of you, well before an engagement actually begins, to know what the most common keybox types are in your area, purchase them and practice on them regularly. If you can defeat the most common keybox types in your area, than there is a very good chance that you will be successful against them on your next engagement.
That said, be extremely cautious if you encounter something like in the image above and not to breach the wrong box as this could lead to both mission failure and a host of legal issues for you and your team.
If you are a team leader, it is vital that you keep good communication with your team and ensure you don’t have a leeroy jenkins on your team who wants to show off by simply breaching them all.
The Overlooked Internal Keybox
The internal keybox represents a more advanced challenge, often doubling as a form of two-factor authentication. These boxes are located within secure areas of a building and contain keys or fobs for further access, such as:
Server rooms
Sensitive document storage
Restricted areas housing critical infrastructure
Unlike their external counterparts, internal keyboxes are generally better protected and monitored. Because they are actually inside the target building, there will usually be employees wandering about, any of whom may notice you attempting to pick a lock, so be cautious and ideally bring a buddy to watch your back.
There also tends to be far more variety with internal keyboxes, ranging from the ridiculously easy to breach, to the actually pretty secure.
While above I said that purchase anything that is common in your area, here is where that likely won’t be possible for many teams as the combination of variety and expense will often be a limiting factor.
That said, you should at least know which brands and models are most common in your area, and have an idea of what you and your team are capable of breaching and which you simply are not.
Keep in mind that companies that go for the internal keybox have already noted the security issue of needing some form of physical two factor authentication and if they have the budget, they will likely spring for the most expensive solution (thanks vendors) … which is an issue all by itself.
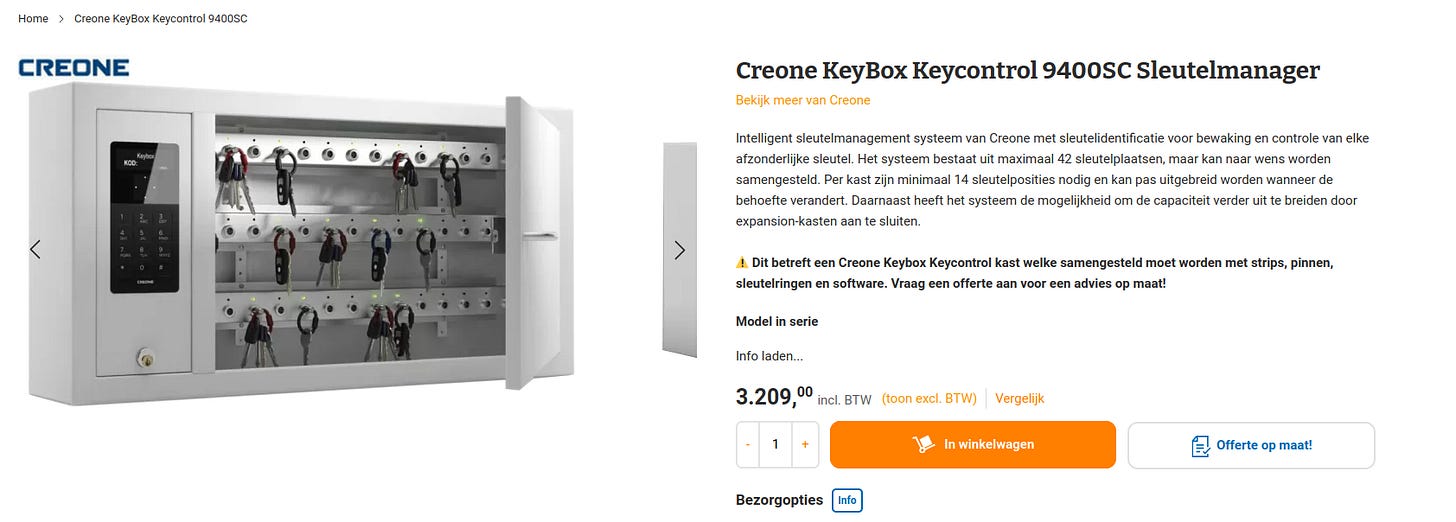
Toys Are Expensive
The above internal keybox solution, which happens to be the smallest and most affordable of this brand, costs 3,200 euros, and as such the owner probably won’t be very happy with you if you go around breaking their keyboxes during a pentest.
It’s one thing to break an external $15 keybox and it is a very different thing to ruin something like the above.
This is why having a good working relationship with your client contact is vital. Once you have breached the building and noticed this expensive beast, unless you are positive, with lots of experience and practice, that you can break into it without damage or destruction, you need to ask the client if you can be allowed to try it and explain the risks.
This is incredibly important for black teams, because what will often occur is that the client will say something like
” You are authorized to break minor, inexpensive things with a total dollar value of XXX”
Which these keyboxes often grossly go beyond the sticker value. Basically, if you have not practiced on these boxes extensively, and can confidently breach them without damage the client likely will not allow you to “give it a shot” and that means this entire attack vector is now off limits to you.
You may have already breached the building, located the classified documents locker and the keybox but have not been authorized to breach the keybox due to expense, which leaves you with either picking the lockers or possibly accepting defeat, unless there happens to be a bypass method.
This is why having a plan for internal keyboxes is important for your team. If the client tells you the goal of the engagement is to gain access to something / someplace and these expensive or complicated keyboxes are a requirement consider the above during the scoping meeting or recon phase.
Don’t Get Treed By A Chiwawa
All of this said, don’t get treed by a chiwawa, which effectively means that just because a keybox looks big, scary or new doesn’t make it secure.
Suppose during an engagement you come across some keybox you have never seen before, its big, looks heavy and expensive and it has no dials, combinations or keyway … what should you do?
Well, because it’s new to you, you cannot confidently say that you have experience breaching it without damage … and therefore you have to err on the side of caution, but that doesn’t mean simply try nothing.
My advice is to explain to the client your situation and what you are wanting to try and get their permission. Only attempt the most safe and secure things that you feel will not damage the device.
I once encountered such a setup on an engagement, and while all of the above scariness of the box was true, it was actually vulnerable to simply latch slipping, which did not damage the device at all.
On another engagement where I encountered a similar situation, the box was so expensive that even simple latch slipping was said to be off limits by the client … but positioning myself in the right spot , waiting for an authorized employee to access the box and having a teammate run a distraction allowed me to grab the key i needed.
Just because you may not be able or authorized to attack an expensive box does not mean that you cannot try some things … but always get the ok by the client.
A Final War Story
I once found myself on an engagement of a very secure facility. When attempting ot enter the building, the client was running, uncloneable badges which had to be paired with a biometric can, inside a one person turn style with an armed guard watching.
Pretty good front door security I would say, unfortunately it was still possible to breach this location in another way which I will leave for another blog post.
But once inside, I found that the client was using internal keyboxes on every floor for authorized personnel to get extremely sensitive documents from various lockers, where each key was associated with a different locker.
After breaching every floor of the target building, gaining access to the interal keyboxes and demonstrating proof that I could access the secure lockers contents the client made a request,
”Please push things as far as you can to see at what point personnel respond”
Up until this point, I had only been taking a single key from a single box at any given time and returning it once used. Now, I decided to take every key from every box just to see what would happen.
The client informed me that their physical SOC was actually contacted by an employee, where I learned the conversation went something like this,
Employee: “I went to get key number X from box number Y and all the keys are missing”
Security: “Huh, well have you checked with other personnel, maybe they are all being used”
Yep, because this had never happened before, security had no SOP for what to do in this situation, and as rediculous as it sounds, even by EOD security was not setting off alarms for the missing keys.
Conclusion
When planning to breach keyboxes, remember that you may encounter a wide variety of types—some simple and others highly advanced—and they can be located both outside and inside the building. Each scenario presents unique challenges and opportunities. Practice with as many different models as possible, focusing on those commonly found in your area. Be especially cautious when approaching newer or more expensive keyboxes, as they often include advanced security features.
And finally, don’t let appearances deceive you. Even a shiny, modern keybox might have vulnerabilities as glaring as an old, rusty lock. In other words, don’t get “treed by a Chihuahua”—keep a sharp, adaptable mindset, and you’ll find the way forward.
Training Resources:
For individuals looking for a hands on training that includes all of the above topics, Covert Access Team (covertaccessteam.com) provides training courses focused on physical penetration testing, lockpicking, bypassing techniques, social engineering and other essential skills.
Covert Access Training - 5 day hands on course designed to train individuals and groups to become Covert Entry Specialists
Physical Audit Training - 2 day course on how to setup and run a physical security audit
Elicitation Toolbox Course - 2 day course of that primarily focuses on elicitation and social engineering as critical aspects of Black Teaming
Counter Elicitation - 2 day course on how to recognize and prevent elicitation attempts, and safegaurd your secrets.
Cyber Bootcamp for Black Teams - 2 day course designed explicitly for physical penetration testers who need vital cyber skills to add to their toolbox.
Private Instruction - Focused learning & training based on your needs .